When we analyzed the top vulnerability scanning tools available, Nmap wasn’t mentioned among them; it isn’t dedicated to those specific tasks but to the entire mapping and reconnaissance process. However, that doesn’t mean it doesn’t offer some great features when it comes to vulnerability scanning.
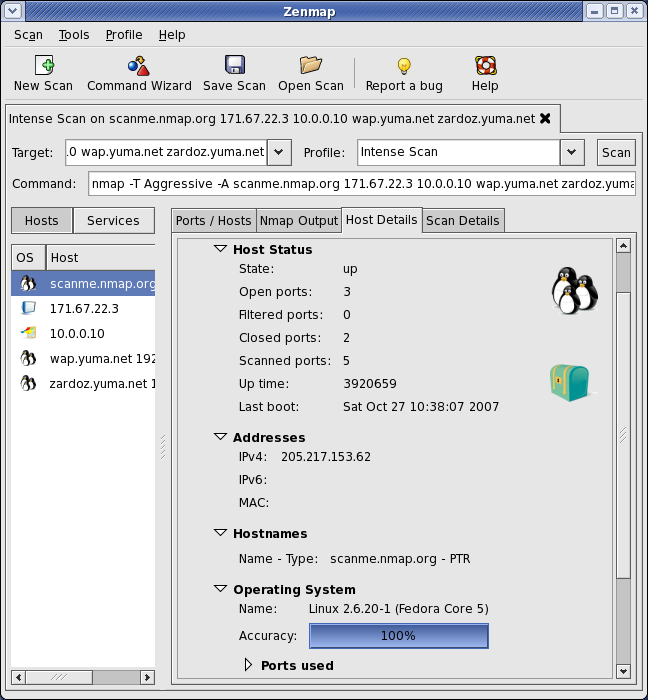
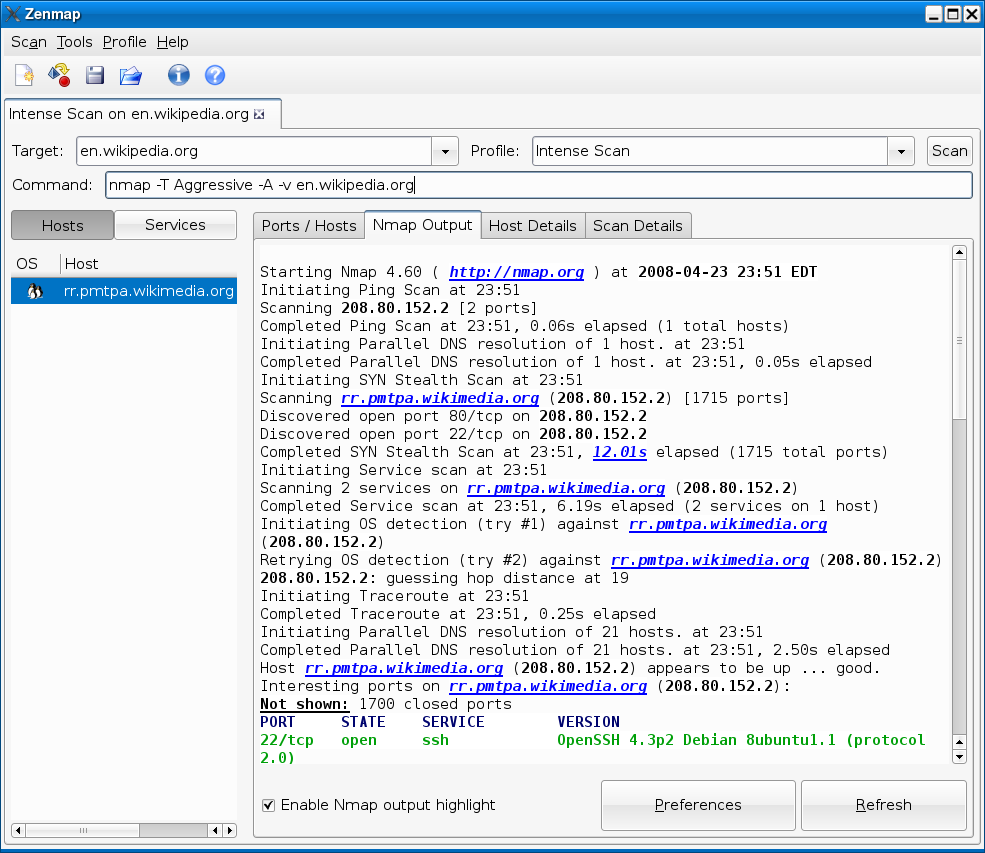
Zenmap is the GUI for the very popular free port scanner Nmap. It comes pre loaded with 10 different scan types which we will take closer look at them in this article. Some of the scan types are kind of obvious, however they may not be to everyone. Nmap was created by Fyodor (Gordon Lyon, twitter, about) and has been actively developed since. Zenmap is the graphical front end for Windows of the network scanning tool called Nmap. Zenmap will allow you to do the same type of scans without having to know the complicated commands or run it from a command/terminal window. Here’s how to install, run a simplae network scan and read it from Zenmap. Different types of scans can be performed: To scan using TCP connect (it takes longer, but is more likely to connect): nmap –sT 192.168.0.1. To perform the default SYN scan (it tests by performing only half of the TCP handshake). Nmap(Network Mapper) is the second program that we're going to look. It is a huge tool and has many uses. Nmap is used to gather information about any device. Using the Nmap, we can gather information about any client that is within our network or outside our network, and we can gather information about clients just by knowing their IP.
Let’s go straight to the fun stuff!
Nmap vulnerability scan using NSE scripts
Nmap is widely known for its famous port mapping capabilities — we love it, and even included it in our best port scanners article a few months ago. Still, it would be quite unfair to reduce Nmap to nothing more than a “network mapper” or “port scanner.”.
Zenmap Tutorial
CVE stands for Common Vulnerabilities and Exposures. In plain English, that simply means it’s a way to organize and categorize software vulnerabilities. This information can be highly useful for security researchers and penetration testers in their daily tasks.
Something we really love about Nmap is its ability to expand its core features by using Nmap scripts. By combining these Nmap commands with a few NSE scripts, we’re able to fetch the most popular CVEs from any target.
Two of the most popular vulnerability/CVE detection scripts found on Nmap NSE are nmap-vulners and vulscan, which will enable you to detect relevant CVE information from remote or local hosts.
Along with those two, the entire “vuln” category is an absolute treasure trove — a truly useful resource when using Nmap as a vulnerability scan engine.
Nmap vulscan
Vulscan queries its own local CVE databases, hosted on the client performing the scan. These local databases include the following files: scipvuldb.csv, cve.csv, securityfocus.csv, xforce.csv, expliotdb.csv, openvas.csv, securitytracker.csv, osvdb.csv.
Zenmap Parameter
In order to use this NSE script, we’ll need to clone its github repo, in almost the same way we did before. How to 123movies on mac.
Installation
The following commands will install the vulscan script along with all the databases mentioned:
Now let’s perform an Nmap vulnerability scan with vulscan, by using the following syntax:
The expected output will show you something like this:
Tip: you can also use your own CVE local database by using the vulscandb argument:
Nmap-vulners
Nmap-vulners is one of the most famous vulnerability scanners in use. Let’s explore how to install this tool, as well as how to perform a simple CVE scan.
Installation
Copy and paste the following two lines to install the nmap-vulners:
Testing
The syntax we’ll be using is pretty simple, calling the script by using –script and specifying the vulners engine, as shown here:
If you want to target specific posts, you simply need to add -p80 at the end, and replace “80” with the port you want to scan. And of course, replace 11.22.33.44 with your desired IP.
You can also target by host name. For example:
Nmap-vulners queries the Vulners exploit database every time we use the NSE script. And here’s the expected output:
As you can see, we were able to discover several CVEs easily, including SSH and BIND vulnerabilities.
Tip: Another way to run these scripts is by combining both of them into one single command, as shown below:
Nmap vuln
The way NSE scripts are defined is based on a list of predefined categories where each script belongs. These categories include: auth, broadcast, brute, default, discovery, dos, exploit, external, fuzzer, intrusive, malware, safe, version, and vuln.
Vuln is the one we’ll be using to launch our next scan against vulnerable subdomains. The syntax is the same as that of the previous NSE scripts, with ‘vuln’ added after ‘–script’, as you can see here:
Expected output:
Here, we launched a CVE scan against port 8443, but you can query other ports, or the entire site as well.
Summary
Nmap’s powerful scripts allow you to not only perform port scanning tasks, but also to discover CVEs in a matter of seconds. Thanks to Nmap, this becomes an easy task, even if you don’t have advanced technical skills.
Are you ready to detect and prevent real cybersecurity threats? Start exploring your entire attack surface area and discover more with SurfaceBrowser™, our all-in-one enterprise-grade tool. Book a demo with our sales team today!
Get the best cybersec research, news, tools,
and interviews with industry leaders
